The benefits of an integrated 3D viewing solution
As a CAD designer, you surely remember the impractical blueprints, the endless meetings, and the guesswork about how part A should actually fit together with part B. With CAD visualization, those days are finally over.
In digital product development, fast and straightforward access to CAD models is crucial. Often, companies face the challenge that CAD models can only be opened and analyzed with special viewers or expensive CAD licenses. This is where the 3D viewer integrated into Cloud PLM comes in – an innovative solution that allows you to visualize, analyze and annotate CAD models.
We will explain here the advantages a 3D viewer offers and why it makes sense to be directly integrated in Cloud PLM:
What is a 3D Viewer?
The 3D viewer is a web-based application that allows CAD models to be displayed, measured, and annotated in three dimensions. The solution opens up new possibilities for collaboration between engineers, designers, suppliers and other stakeholders.
Applications for CAD visualization
- Product development: Designers and engineers can analyze and improve models faster.
- Supplier and customer communication: Models can be shared and discussed without partners needing special CAD software.
- Quality assurance: Testing and approval processes are accelerated by direct measurement in the cloud and the commenting function.
- Technical support and maintenance: Technicians can access 3D models to identify spare parts or perform repairs.
Advantages of 3D viewers Integrated directly into Cloud PLM
1. Cross-CAD system support:
The 3D viewer can display models from different CAD systems, for example, SolidWorks, CATIA, Siemens NX, or Autodesk Inventor. No native software is needed for this.
2. No CAD viewer licenses required:
Access to CAD models is often associated with high licensing costs. 3D viewers integrated in Cloud PLM eliminate this hurdle, as no additional licenses are required. This saves costs and makes it easier to provide the software to a large group of users.
3. Measurement and analysis:
With the 3D viewer, users can measure models directly in the cloud, create cross-sections, and perform analyses. This enables a quick verification of dimensions and tolerances even without access to a CAD system.
4. Collaborative annotation and feedback:
The tool allows users to leave comments and annotations on specific areas of a 3D model. Teams collaborate more efficiently and discuss changes directly on the object.
5. Easier tracking of version status:
The 3D viewer is fully integrated into a cloud-based PLM system. CAD models are called up and edited from within the PLM software. This facilitates management and ensures access to the correct version status.
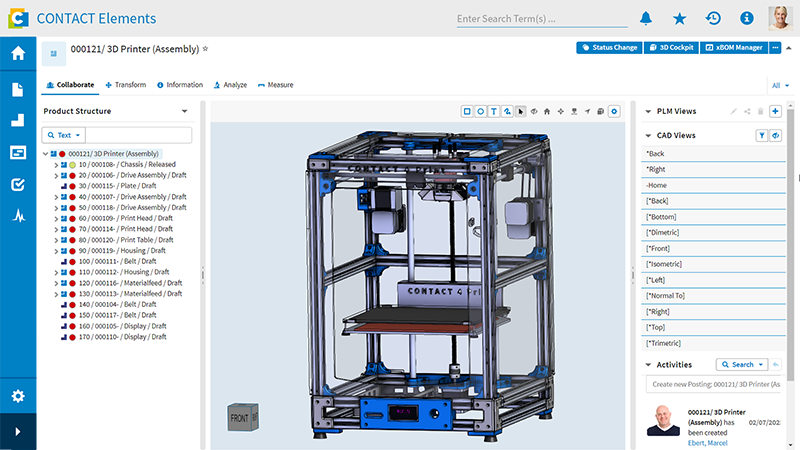
What is CONTACT Elements 3D Connect?
CONTACT Elements 3D Connect offers a comprehensive 3D visualization solution that is integrated into the CIM Database Cloud PLM system. Employees from other specialist departments do not need to install any additional software, but use the viewer directly via the cloud platform. The tool automatically generates a 3D representation based on the checked-in CAD models and offers direct access to CAD model data, parts, variants, product structures and bills of materials. You can use measuring functions, exploded views and redlining and save snapshots of selected views. Color codes reflect component properties such as the release status directly in the model.
Conclusion
The integrated 3D visualization in Cloud PLM removes barriers, reduces costs, and accelerates processes. Cross-CAD system support, the elimination of licenses, as well as the analysis and commenting functions simplify collaboration between all parties involved and increase efficiency. Integration into a cloud-based PLM system ensures that the latest version statuses are always available and product development is optimally supported.
Learn more about the possibilities of 3D Collaboration in CIM Database Cloud.