Ensuring flexibility in Product Lifecycle Management
Product Lifecycle Management (PLM) has evolved rapidly in recent years. The availability of cloud solutions based on Software-as-a-Service (SaaS) now allows companies of all sizes to implement PLM and scale as needed quickly. This enables even small and medium-sized businesses to realize the benefits of PLM, such as improved collaboration, more efficient processes, and faster innovation.
However, the move to the Cloud also presents a challenge: customizing. The question is: How do companies ensure that their PLM system meets their specific business requirements?
This blog post shows you how to make your PLM platform more flexible using the customization options of the SaaS Functions Framework.
What is the SaaS Functions Framework?
The SaaS Functions Framework is a collection of architectures, best practices, and guidelines that simplifies and optimizes the creation and operation of SaaS applications. It offers the ability to customize the standard functions of cloud-based PLM systems, such as CIM Database Cloud, using special tools and interfaces, without changing the core code of the application.
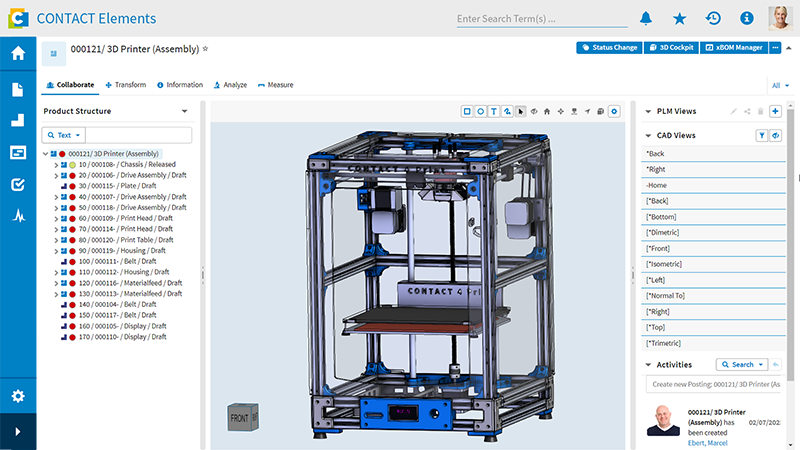
How is the SaaS Functions Framework used in CIM Database Cloud?
The SaaS Functions Framework allows our customers to execute custom code within CIM Database Cloud without having to worry about deploying or maintaining their servers. This is ensured by a serverless infrastructure, which allows customer-specific logic to be implemented directly in the Cloud.
The responsibility for creating, maintaining, and the code of these functions lies with the customer company. The features they develop run independently of updates that CONTACT Software makes to the cloud PLM system. To simplify development, a Software Development Kit is available, allowing for quick and efficient implementation of individual business logic.
Why is customizing important in Cloud PLM?
In the past, companies were bound to rigid, monolithic architectures in on-premises PLM systems. Consequently, customizations were often costly, time-consuming, and risky, especially when they required deep changes to the core code. Customizing tools like the SaaS Functions Framework offer a more flexible and agile alternative in Cloud PLM:
- Customization without compromise: Your company can tailor the PLM solution to its specific needs while retaining the advantages of a cloud-based platform (scalability, automatic updates, lower IT costs, etc.).
- Faster time-to-value: By reusing predefined functions and with easy integration, you can develop and deploy new features faster.
- Promote innovation: Empower your teams to experiment with new technologies and processes without compromising system stability.
- Future-proofing: The SaaS Functions Framework allows for the continuous enhancement of your PLM solution and its adaptation to evolving business requirements.
Application examples of the SaaS Functions Framework in CIM Database Cloud
The SaaS Functions Framework…
- …ensures easy ERP integration. This is achieved using webhooks, an industry standard for automatic, event-driven, real-time communication between web applications.
- …promotes the implementation of custom business logic, such as input validations and dependency checks. For example, you can ensure that an item can only be released once the associated specification document is available and the item numbers consistently correspond to the number ranges of the item category.
- …supports the development of custom automations. For example, document titles can be automatically generated from the associated item names. You can also obtain item numbers from the ERP system or define mandatory fields depending on the item category.
- …enables individually designed reporting.
- …allows the editing of files, such as stamping metadata into documents after release (approver, release date) and the creation of neutral formats.
Conclusion
Unlocking the full potential of Cloud PLM systems requires seamless integration into individual business processes. The CONTACT CIM Database Cloud Functions Framework serves as the ideal bridge here. Companies can tailor and expand their Cloud PLM platform as needed to meet changing requirements, without sacrificing the benefits of the Cloud.
CONTACT SaaS Functions Frameworks offer you the possibility to execute custom code directly in the Cloud.